If someone would like to analyze network traffic of Voice over IP or Video over IP the starting point is to make sniffs. Although this is quite a straightforward process there are some point so be marked and keep in mind.
Start with WireShark. This is a very powerful tool and you will get help very easily if you get stuck. First you have to select the appropriate Interface to make the sniff.
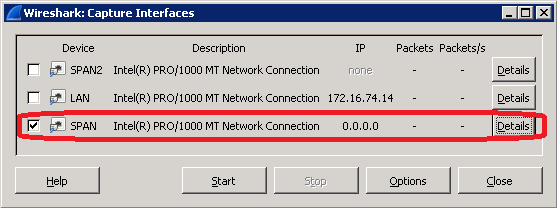
Generally we do not want to sniff the normal network traffic of this specific machine rather we are interested of the traffic of some Phone or Telepresence devices.
I will explain it in a later passage how to redirect these Voice and Video packets to a specific interface. Now we assume that this has been done already.
The next step is to set the options of the sniffing.
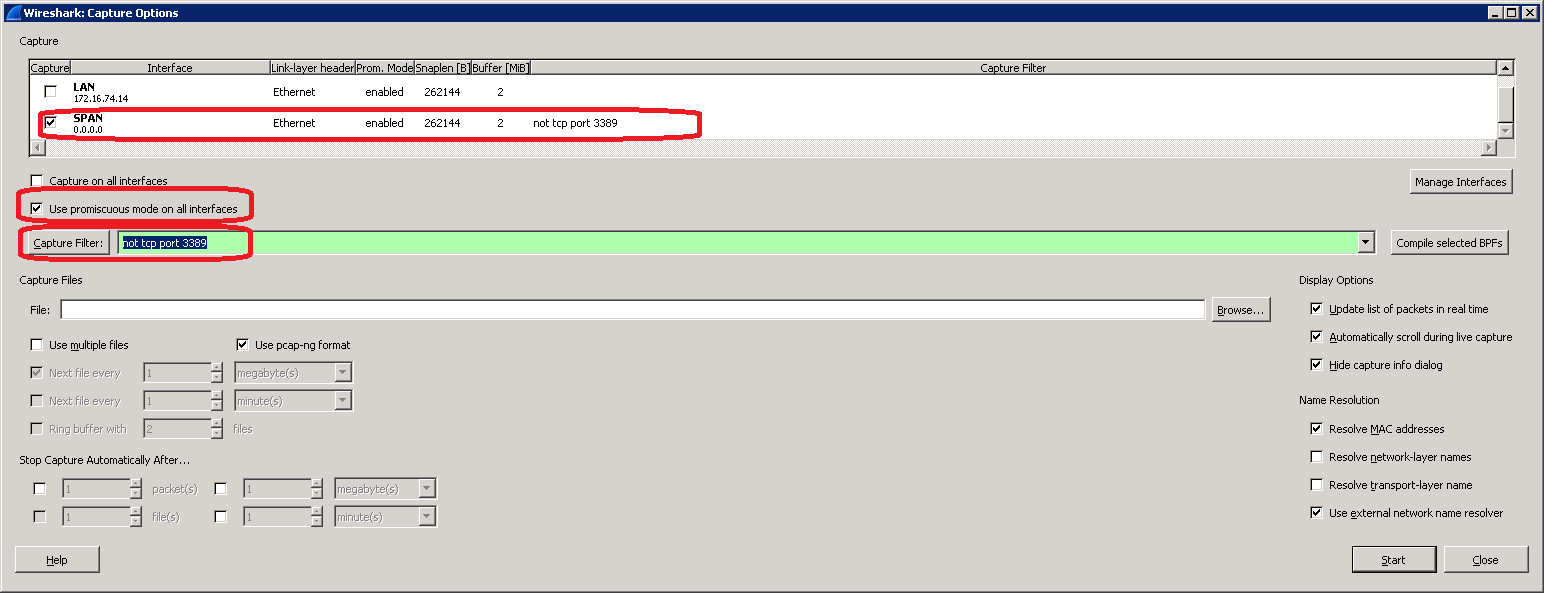
Use promiscuous mode to capture packets which can be seen on this interface.
On the Capture Filter field we can set up specific filters.
In CARIN365 we use the following Capture filters:
- CaptureFilterSignaling for Cisco SKINNY protocol: (tcp port 2000)
- CaptureFilterSignalingSip for SIP protocol: (port 5060)
- CaptureFilterSignalingH323 for H232 signaling protocol: (tcp port 1720)
The packet capture interface prepares a compiled filter according to these settings like this:
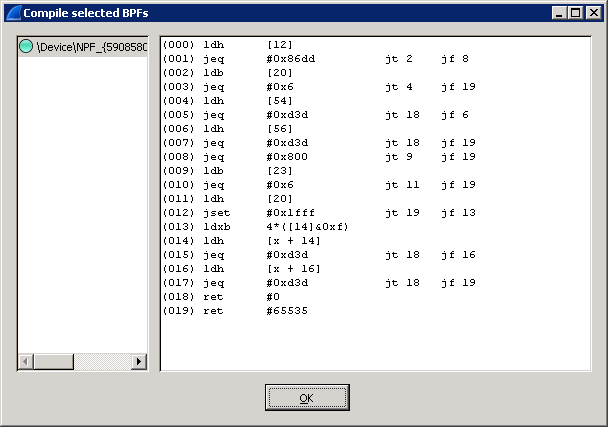
This is a very efficient real time filter and shall not be mixed up with the offline filter during the analysis phase.
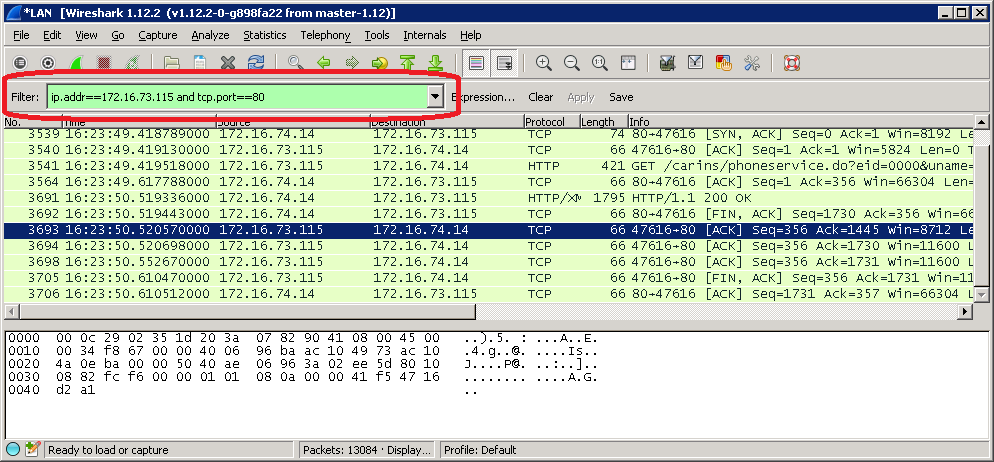
Once we have the sniff we can analyze it immediately or save it for a later usage.
If we process it later on with CARIN365 tools we have to save it in TCP Dump format which is the second option in the save list.
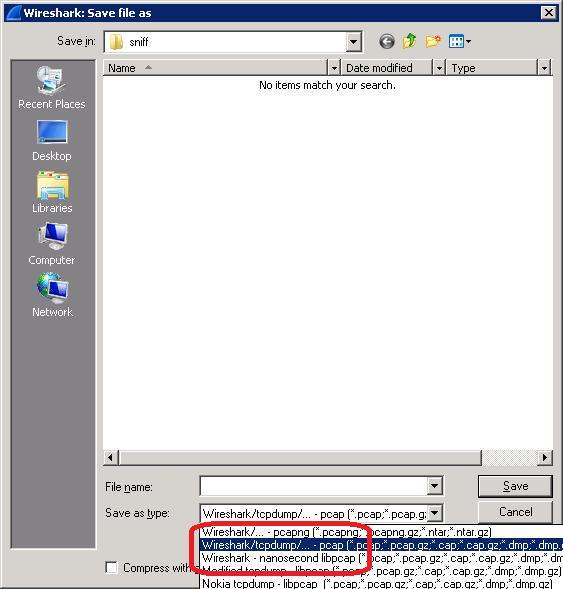
How to go further in depth with the sniff I will discuss in the next session.
Try it, play with it. This is the way how the “Homo Ludens” acquires knowledge.












